Commercial Grade Antivirus
Advanced antivirus solutions to detect and remove malware.
A range of cyber security solutions, including Essential 8 mitigations.
Hackers most commonly get access to your systems via compromised email.
Once in, they can spread through your network encrypting, damaging and stealing your valuable data.

As reported to ReportCyber in 2023, $80 million in losses were facilitated by business email compromise fraud.*
Advanced antivirus solutions to detect and remove malware.
Continuous monitoring and quick response to suspicious activities.
Guards networks, manages traffic, & enforces security policies.
Manage individual user controls and ensure authorized access only.
Store credentials securely and prevent unauthorized access & theft.
Isolated network segments reduce the risk of breaches spreading.
Regular and secure backups, with a tested a restoration process.
Safeguard against phishing, spam, & other email-based threats.
Ensure recognition & understanding of risks and security best practices.
Round-the-clock monitoring and support to address issues promptly.
Assessments & assurance of systems and software to harden security.
To find out more about our full range of services, check out the packages we currently have on offer.
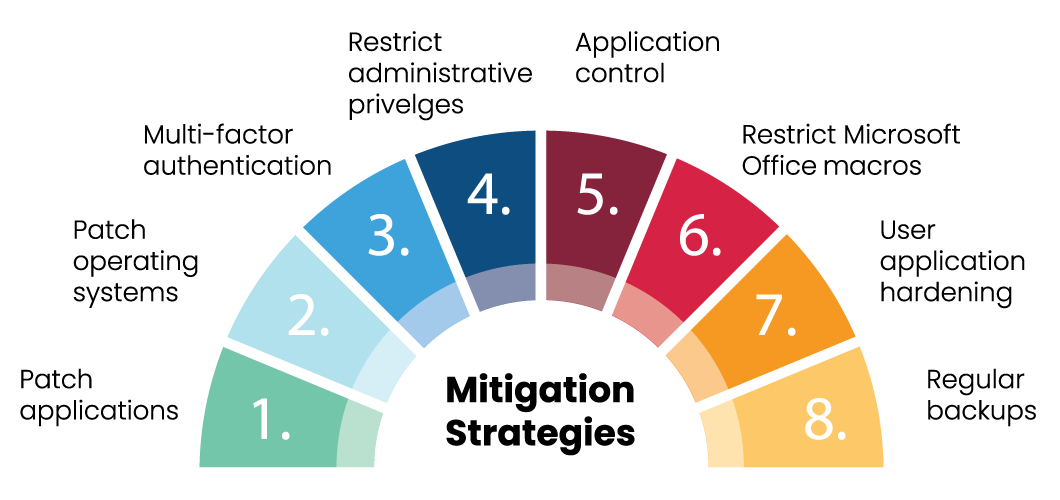
Developed and maintained by the Australian Cyber Security Centre (ACSC), the Essential 8 comprises a checklist of eight core mitigation strategies which target vulnerable systems, applications and devices.
Attackers can exploit application security flaws, as outdated software can expose systems to significant risks.
Using the latest OS is crucial to preventing attackers from exploiting flaws that could lead to security breaches.
Requires users to verify their identity with two methods, making it harder for attackers to gain unauthorized access.
Disabling access & using unique passphrases prevents attackers from easily spreading across a network.
Stops unapproved or malicious software running on systems, from downloads, attachments, or removable media.
Vetting macros helps prevent attackers from using them to run malicious code and bypass basic security measures.
Disabling unneeded features and blocking risky web content and code, helps prevent exploitation of vulnerabilities.
Essential to protect against data loss from ransomware, hardware failure, or other destructive events.
The Essential 8 mitigation strategies are used to facilitate the desired Maturity Level.
Each level is designed to address progressively more sophisticated threats.

You select the maturity level that aligns with the cyber security posture your organization aims to achieve.
Then we will help you achieve your goal.
Your IT Crew specializes in robust cyber security solutions, ensuring that your systems are protected against the latest threats with a proactive approach.
We offer comprehensive end-to-end IT services, from initial assessments and planning to implementation and ongoing support, covering all your technology needs.
With extensive experience and a team of experts, Your IT Crew delivers reliable and effective IT solutions tailored to meet your specific business requirements.
Your IT Crew is a trusted partner to many leading businesses, providing reliable, industry-best cybersecurity tools and services tailored to meet their specific needs.

Find out how Your IT Crew can help your business manage risk, respond to incidents and strengthen your general cyber security posture.
